Sunday, June 18, 2023
Please Confirm
I'm Dr. Bengat. I wish to urgently confirm from you if actually you know one Mrs. Jeanne White who claims to be your business associate/partner.
Kindly reconfirm this application put in by Mrs. Jeanne White - she submitted the under-listed bank account information supposedly sent by you to receive the funds on your behalf.
The bank information she applied with are stated thus:
Account Name: Mrs. Jeanne White
Bank name: Citi Bank NA
Bank address: #1230 Arch Street, Philadelphia, PA 19107, USA
Account Number: 013439887655
Routing Number: 2771722
Swift Code: CITIUS30
The said Mrs. Jeanne White is claiming to this office that you are dead and have Instructed that all relevant documentation/Information regarding your Payment/Transfer, be changed to her as the beneficiary of the payment short-listed among the foreign beneficiaries entitled to receive their payment.
For your Information, this Government has approved the total amount of EIGHT MILLION, FIVE HUNDRED THOUSAND UNITED STATES DOLLARS ONLY, in your favor, prior to the Federal Government instructions/mandate to offset all outstanding payments to the various legal foreign beneficiaries. We need to confirm from you if it's really true that you are dead as mentioned by your Associate.
You should note that, if we do not hear from you, we automatically assume that you are actually dead and the information passed to us by Mrs. Jeanne White is correct. Hence, you are hereby requested to reply to this Email immediately for confirmation, before we proceed with this payment and for us to know the true position of things with you so that we won't make any mistakes/errors in remitting your out-standing payment to a wrong person/account.
Lastly, you are advised to reply back to this email and reconfirm the details of this message if truly you're alive.
Full name................................
Direct telephone number.........
Address....................................
Age...........................................
Your quick response will help us a lot ( lorenzobengat@aliyun.com )
Yours, Sincerely,
Dr. L. Bengat
Monday, June 5, 2023
$$$ Bug Bounty $$$
A bug bounty program, also called a vulnerability rewards program (VRP), is a crowdsourcing initiative that rewards individuals for discovering and reporting software bugs. Bug bounty programs are often initiated to supplement internal code audits and penetration tests as part of an organization's vulnerability management strategy.
Many software vendors and websites run bug bounty programs, paying out cash rewards to software security researchers and white hat hackers who report software vulnerabilities that have the potential to be exploited. Bug reports must document enough information for for the organization offering the bounty to be able to reproduce the vulnerability. Typically, payment amounts are commensurate with the size of the organization, the difficulty in hacking the system and how much impact on users a bug might have.
Mozilla paid out a $3,000 flat rate bounty for bugs that fit its criteria, while Facebook has given out as much as $20,000 for a single bug report. Google paid Chrome operating system bug reporters a combined $700,000 in 2012 and Microsoft paid UK researcher James Forshaw $100,000 for an attack vulnerability in Windows 8.1. In 2016, Apple announced rewards that max out at $200,000 for a flaw in the iOS secure boot firmware components and up to $50,000 for execution of arbitrary code with kernel privileges or unauthorized iCloud access.
While the use of ethical hackers to find bugs can be very effective, such programs can also be controversial. To limit potential risk, some organizations are offering closed bug bounty programs that require an invitation. Apple, for example, has limited bug bounty participation to few dozen researchers.
Related news
- Hack Tools
- Pentest Recon Tools
- Wifi Hacker Tools For Windows
- Pentest Tools Apk
- Hacking Tools 2020
- Hacking Tools 2020
- Best Hacking Tools 2019
- Pentest Tools Apk
- Top Pentest Tools
- Hack Tools Online
- Pentest Tools Review
- Hacker Tools 2020
- Pentest Tools Find Subdomains
- Pentest Tools Linux
- How To Install Pentest Tools In Ubuntu
- Install Pentest Tools Ubuntu
- Pentest Tools Framework
- Hacking Tools 2019
- Hacking Tools For Windows 7
- Blackhat Hacker Tools
- Hacker Tools Github
- Hacker Tools Software
- Pentest Tools Apk
- Hacking App
- Pentest Tools Linux
- Hacking Tools Kit
- Hackrf Tools
- Hacking Tools Software
- How To Hack
- Ethical Hacker Tools
- Pentest Tools For Ubuntu
- Hacking Apps
- World No 1 Hacker Software
- Hacker Tools 2020
- Hacker Techniques Tools And Incident Handling
- Hacker Search Tools
- Hack Rom Tools
- Hack Tools Github
- Github Hacking Tools
- Pentest Tools For Android
- Hack Tool Apk No Root
- Free Pentest Tools For Windows
- Hacker Tools Software
- Best Hacking Tools 2019
- Tools For Hacker
- Pentest Tools Online
- Tools Used For Hacking
- Hack Rom Tools
- Pentest Automation Tools
- Pentest Tools For Windows
- Hack Tools For Windows
- Black Hat Hacker Tools
- Pentest Tools Windows
- Hacker Tools 2020
- Hacker Tools Free Download
- Nsa Hacker Tools
- Hacker Tools 2019
- Tools Used For Hacking
- Pentest Tools Bluekeep
- Hacker Tools Software
- Hacker Tools Online
- Pentest Tools Url Fuzzer
- Pentest Tools Kali Linux
- Hacking Tools Pc
- Pentest Tools For Windows
- Hack Apps
- Hacker
- Pentest Tools Free
- Hacking Tools For Windows 7
- Free Pentest Tools For Windows
- Pentest Tools Open Source
- Pentest Tools Kali Linux
- Hacker Tools Free
- Pentest Tools Windows
- Pentest Tools Bluekeep
- Hacker Hardware Tools
- Hak5 Tools
- Hack Tools For Windows
- Pentest Tools Review
- Pentest Tools Online
- Pentest Tools Online
- Hack Tools For Ubuntu
- Wifi Hacker Tools For Windows
- Nsa Hack Tools
- Tools 4 Hack
- Usb Pentest Tools
- Hack Tools Online
- Ethical Hacker Tools
- New Hacker Tools
- Pentest Tools Framework
- Hack Tools
- Pentest Tools Port Scanner
- Hack Tools 2019
- What Are Hacking Tools
- Pentest Reporting Tools
- Pentest Tools Find Subdomains
- Hacker Techniques Tools And Incident Handling
- Pentest Tools For Mac
- Pentest Tools For Mac
- Hack Tools
- Hacker
- Hacking Tools For Games
- Hack Tools For Ubuntu
- Pentest Tools Framework
- Tools For Hacker
- Hack Tools For Games
- Best Hacking Tools 2019
- Hacker Tool Kit
- Hack Tool Apk
- Hack Tools 2019
- Hack Rom Tools
- Kik Hack Tools
- Hack Tools 2019
- Pentest Tools For Windows
- Kik Hack Tools
- Hacking Tools For Windows Free Download
- Hacker Tools Mac
- Physical Pentest Tools
- Hacking Tools Windows
- Tools For Hacker
- Hacker Techniques Tools And Incident Handling
- Pentest Tools Port Scanner
- Termux Hacking Tools 2019
- Pentest Automation Tools
- Hacker Tools Mac
- Hacker Tools Linux
- Hacker Tools Apk Download
- Best Hacking Tools 2020
- Pentest Tools Download
- Hacking Tools Github
- Hacking Tools Mac
Multi-Protocol Proxy Over TCP & UDP
Many years ago I programed a console based multi protocol proxy (the sha0proxy) lately I created in dotnet a graphical verison of the tool, but due to the form referesh speed finally I implemented it in C++ with Qt.
This tool useful for reversing, exploiting & pentesting was finally called rproxy, and its a multi-protocol proxy over TCP or UDP.
Being in the middle of the communication you can view and modify the bytes before being sent to the client or server.
In the tools tab right now its possible to open the blob on radare2 for further reversing of the data structures or code.
A basic mutation based fuzzer is implemented for bug-hunting, just set the % ratio of mutation and the bytes will be modified during specific communications phase.
One of the powerful things of this tool is the scripting, it is possible to automate a modification in specific moment of the traffic flow.
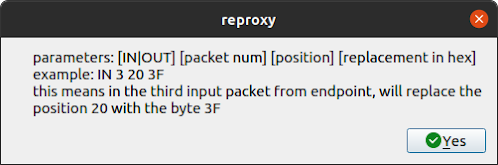
For example a script with a single line: "IN 3 20 3F" will write a 0x3f on the offset 20 only on the third packet received from the server. I have used this feature for triggering vulnerabilities.
Regarding the saving and loading data from disk, it's possible to save and load data in raw and hex formats. Also can be configured for save all the communications or only specific emission.
Related word
- Pentest Tools Website Vulnerability
- Hacking Tools For Windows Free Download
- Hack Tools Github
- Pentest Tools Alternative
- Tools 4 Hack
- Pentest Tools List
- Pentest Tools Linux
- Hack And Tools
- Pentest Tools Port Scanner
- Hacking Tools For Pc
- Hacking Tools And Software
- Hacking Tools For Kali Linux
- Pentest Tools Linux
- Termux Hacking Tools 2019
- Termux Hacking Tools 2019
- New Hacker Tools
- Wifi Hacker Tools For Windows
- Pentest Tools Windows
- Hack Tools For Games
- Pentest Automation Tools
- Hacker Tools Hardware
- Black Hat Hacker Tools
- Pentest Tools Kali Linux
- How To Make Hacking Tools
- Hacker Tools Github
- Hack Tool Apk No Root
- Hacking Tools For Windows Free Download
- Hacker Tools Github
- Pentest Tools Url Fuzzer
- Hacking Tools Kit
- Hack Tools Pc
- Nsa Hacker Tools
- Pentest Tools Apk
- Pentest Tools Bluekeep
- Pentest Tools Port Scanner
- Hacking Tools And Software
- How To Make Hacking Tools
- Hack Tools Online
- Hacker Tools
- Hacking Tools
- Pentest Tools Port Scanner
- Computer Hacker
- Pentest Tools
- Hacker Tools
- Hacker Tools 2019
- Nsa Hack Tools
- Pentest Tools For Mac
- Pentest Box Tools Download
- Pentest Tools Alternative
- Beginner Hacker Tools
- Hacker Tools Free
- Tools 4 Hack
- Hacker Tools 2020
- Tools For Hacker
- Hack Tools 2019
- Pentest Tools Windows
- Hacking Tools And Software
- How To Hack
- Hacking Tools 2020
- Pentest Tools Framework
- Hacker Tools For Windows
- Hacking Tools Usb
- How To Hack
- Hacking Tools Software
- Hacker Tools Free Download
- Pentest Tools Apk
- Hacking Tools For Windows 7
- Growth Hacker Tools
- Hack Tools Pc
- Bluetooth Hacking Tools Kali
- Pentest Tools Url Fuzzer
- Pentest Tools Subdomain
- Pentest Tools Website
- Best Pentesting Tools 2018
- Pentest Tools Alternative
- Hacker Tools List
- Hackers Toolbox
- Pentest Tools Tcp Port Scanner
- Easy Hack Tools
- Hacker Tools List
- Hack Tool Apk
- Hack Website Online Tool
- Pentest Tools For Ubuntu
- Hacker Tools Free Download
- Hack Tools Github
- Hacker Tools
- Hack Tools For Pc
Sunday, June 4, 2023
Ophcrack
 " Ophcrack is an open source (GPL license) program that cracks Windows LM hashes using rainbow tables. The program includes the ability to import the hashes from a variety of formats, including dumping directly from the SAM files of Windows. There is also a Live CD version which automates the retrieval, decryption, and cracking of passwords from a Windows system. Rainbow tables for LM hashes of alphanumeric passwords are provided for free by the developers. These tables can crack 99.9% of alphanumeric passwords of up to 14 characters in usually a few seconds, and at most a few minutes. Larger rainbow tables (for LM hashes of passwords with all printable characters, including symbols and space) are available for purchase from Objectif Securité. Starting with version 2.3, Ophcrack also cracks NT hashes. This is necessary if generation of the LM hash is disabled (this is default on Windows Vista), or if the password is longer than 14 characters (in which case the LM hash is not stored)." read more...
" Ophcrack is an open source (GPL license) program that cracks Windows LM hashes using rainbow tables. The program includes the ability to import the hashes from a variety of formats, including dumping directly from the SAM files of Windows. There is also a Live CD version which automates the retrieval, decryption, and cracking of passwords from a Windows system. Rainbow tables for LM hashes of alphanumeric passwords are provided for free by the developers. These tables can crack 99.9% of alphanumeric passwords of up to 14 characters in usually a few seconds, and at most a few minutes. Larger rainbow tables (for LM hashes of passwords with all printable characters, including symbols and space) are available for purchase from Objectif Securité. Starting with version 2.3, Ophcrack also cracks NT hashes. This is necessary if generation of the LM hash is disabled (this is default on Windows Vista), or if the password is longer than 14 characters (in which case the LM hash is not stored)." read more...Website: http://ophcrack.sourceforge.net
Related links
- Pentest Recon Tools
- Pentest Tools
- Hak5 Tools
- Blackhat Hacker Tools
- Hacker Tools Apk Download
- Hack Website Online Tool
- Pentest Automation Tools
- Hacker Tools
- Pentest Tools Alternative
- Pentest Tools Bluekeep
- Hacking Tools For Beginners
- Tools For Hacker
- Pentest Tools Website Vulnerability
- Hacking Tools For Beginners
- Hacker Tools Github
- Nsa Hacker Tools
- Termux Hacking Tools 2019
- Hackers Toolbox
- Pentest Tools For Mac
- Hacker
- Hack Tools
- Hack Tools Mac
- Wifi Hacker Tools For Windows
- Pentest Tools List
- Wifi Hacker Tools For Windows
- Hack Website Online Tool
- Hack Tools Download
- Hacker Techniques Tools And Incident Handling
- Hacker Tools List
- Nsa Hack Tools Download
- Tools Used For Hacking
- Best Hacking Tools 2020
- Hacking Tools Free Download
- Hacking Tools For Beginners
- Hack Apps
- Hack Tools For Windows
- Hack Tools For Windows
- Pentest Tools Bluekeep
- Beginner Hacker Tools
- Hacker Tools Free
- Android Hack Tools Github
- Hacker Tools Github
- Hack App
- Hacker Tools 2020
- Pentest Tools List
- Nsa Hacker Tools
- Best Pentesting Tools 2018
- Best Pentesting Tools 2018
- Pentest Tools Github
- Best Pentesting Tools 2018
- Game Hacking
- World No 1 Hacker Software
- Hacker Tool Kit
- Game Hacking
- Hacker Tools For Windows
- Hacker Techniques Tools And Incident Handling
- Tools For Hacker
- Hack Tools For Windows
- Hacking Tools For Beginners
- What Is Hacking Tools
- Computer Hacker
- Hack Rom Tools
- Ethical Hacker Tools
- Hacking Tools For Windows
- Bluetooth Hacking Tools Kali
- Hack Tools
- Hacker Tools For Windows
- Pentest Box Tools Download
- Pentest Tools Linux
- Hacker Tools Windows
- Hack Tools
- Game Hacking
- Hacking Tools 2019
- Pentest Tools Linux
- Hacking Tools Github
- Pentest Tools Windows
- Hack And Tools
- Pentest Tools Port Scanner
- Pentest Tools Bluekeep
- Hak5 Tools
- Pentest Tools Bluekeep
- Growth Hacker Tools
- Pentest Tools For Ubuntu
- Pentest Tools For Windows
- How To Make Hacking Tools
- Hacking Tools 2020
- Hacks And Tools
- World No 1 Hacker Software
- Pentest Tools Find Subdomains
- Hacking Tools Online
- Hacking Tools Download
- Pentest Tools Nmap
- Hacker Tools Github
- Hack Tools For Pc
- Pentest Tools Online
- What Are Hacking Tools
- Beginner Hacker Tools
- Game Hacking
- Hacking Tools Usb
- Pentest Tools Website Vulnerability
- New Hack Tools
- Hacking Tools For Kali Linux
- Pentest Tools Online
- Hacking Tools Download
- Hacker Security Tools
- Top Pentest Tools
- Pentest Tools For Windows
- Hack Tools For Pc
- Hacking Tools For Windows
- Pentest Tools Nmap
- Hacking Tools Free Download
- Hackers Toolbox
- Hack Rom Tools
- Hacking Tools Hardware
- Tools Used For Hacking
- Hacker Tools For Mac
- Hacker Tools Windows
- Hacker Tools For Pc
- Hacker Security Tools
- Hacking Tools Mac
- Hackrf Tools
- Easy Hack Tools
- Hacking Tools Usb
- Tools Used For Hacking
- Hacking Tools Software
- Hacker Tool Kit
- Hacking Tools And Software
- How To Make Hacking Tools
- Best Hacking Tools 2019
- Hack Tool Apk
- Hacking Tools For Pc
- Hack Website Online Tool
- Hacker Security Tools
- Hacking Tools For Kali Linux
- Underground Hacker Sites
- Hack Tools For Ubuntu
- How To Hack
- Pentest Tools Tcp Port Scanner
WHO IS ETHICAL HACKER
A hacker is a Creative person and a creative Programmer,who have knowledge about Networking,Operating system,hacking & a best creative social engineer who control anyone's mind he is also a knowledgeable person.
- Game Hacking
- Hacker Tools Apk Download
- Hacker Tools For Windows
- Hacking Tools For Kali Linux
- Pentest Tools Apk
- Bluetooth Hacking Tools Kali
- Hacking Tools Usb
- Hack Tools Pc
- Pentest Tools For Android
- Hacking Tools Usb
- Hacking Tools Download
- Pentest Tools For Ubuntu
- Hacker Tools Software
- Pentest Tools Open Source
- Kik Hack Tools
- Hacker Tools 2020
- Hack Tools Github
- Hacker Security Tools
- Pentest Tools Tcp Port Scanner
- Hacker Tools
- Best Hacking Tools 2019
- Black Hat Hacker Tools
- Pentest Tools Github
- Nsa Hack Tools Download
- Hacker Tools For Pc
- Pentest Tools Free
- Physical Pentest Tools
- Bluetooth Hacking Tools Kali
- Hacking Tools 2020
- Pentest Automation Tools
- Hack Tools 2019
- Computer Hacker
- Hack Tool Apk No Root
- Hacking Tools Kit
- How To Install Pentest Tools In Ubuntu
- Hacker Tools Apk Download
- How To Hack
- Hacker Tools Linux
- Tools For Hacker
- Pentest Tools Website Vulnerability
- Hacker Tool Kit
- Pentest Tools Alternative
- Pentest Tools List
- Hak5 Tools
- Pentest Tools For Windows
- Pentest Recon Tools
- Github Hacking Tools
- Hacker Tools Apk Download
- Hacking Tools Name
- Tools 4 Hack
- Hacker Tools
- Easy Hack Tools
- World No 1 Hacker Software
- Hacker Tools Mac
- Pentest Tools Download
- Hack Tools
- Pentest Tools Tcp Port Scanner
- Best Hacking Tools 2020
- Hacking Tools Free Download
- Hacker Tools Apk
- Hacker Tools
- Best Pentesting Tools 2018
- Pentest Tools For Android
- Hacking Tools And Software
- Pentest Tools Bluekeep
- World No 1 Hacker Software
- Hack Tools Download
- Hacks And Tools
- Pentest Tools Framework
- Install Pentest Tools Ubuntu
- Pentest Tools For Android
- Hacker Tools Free Download
- Pentest Tools Android
- Hacker Tool Kit
- Nsa Hack Tools
- Ethical Hacker Tools
- Hacker Tools Apk
- Hack App
- Hacker Tools Apk Download
- Hacking Tools Free Download
- Hacking Tools Github
- Pentest Tools For Android
- Hacker Tools For Mac
- Nsa Hacker Tools
- Top Pentest Tools
- Pentest Tools
- Kik Hack Tools
- Hack Tools Pc
- Pentest Tools Open Source
- Hack Tools Github
- Hack Tools For Mac
- Hacking Tools Online
- Hackers Toolbox
- Hacker Tools Linux
- Hacker Tools For Mac
- Hacker Tools 2019
- Nsa Hacker Tools